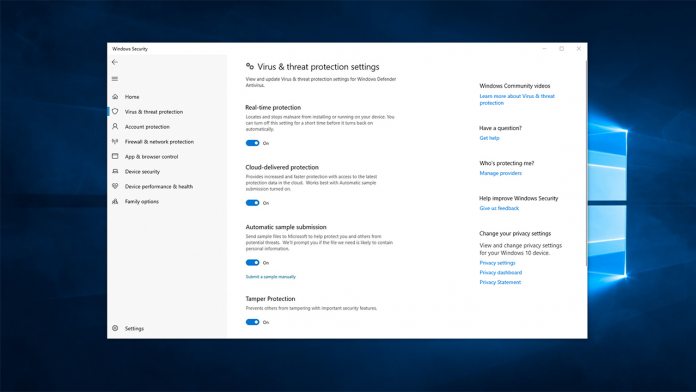
To do so, it ensures malicious apps can’t make changes to the registry, via PowerShell cmdlets, and by adjusting group policies. It has been available to Windows Insiders since late 2018, but this signals its readiness for wide deployment. As well as Windows, Tamper Protection is available in Microsoft Defender Advanced Threat Protection. This is Microsoft’s enterprise-grade tool that uses techniques like heuristic analysis to discover threats that traditional AVs would miss.
Locking Out the End-User
It’s here that Tamper Protection really shines. Toggling the feature on Workstations stops end-users as well as malware from changing settings, cutting out the issue of user error. According to ZDNet, Tamper Protection will be enabled by default with its full release, though consumer Windows users can toggle it off if they wish. Meanwhile, enterprise admins will have to manage their AV features via Intune. If a user does try to change AV settings, the admin will be notified immediately. Of course, all of this is contingent on users keeping their operating system up to date. You’ll need to be on the Windows 10 May update (1903) to access the powerful protection feature. All users should ensure they’re up to date for security reasons but this is another push to upgrade to the latest version of Microsoft’s OS.