“The open-source nature of the Android OS makes it possible for manufacturers to ship custom versions of the OS along with a set of pre-installed apps, often for product differentiation,” said the researchers. “Some device vendors have recently come under scrutiny for potentially invasive private data collection practices and other potentially harmful or unwanted behavior of the preinstalled apps on their devices. Yet, the landscape of preinstalled software in Android has largely remained unexplored.” The study finally offers that exploration and the results aren’t positive. According to the study, Android’s model has led to practices that could pose a security risk or be used to install backdoors.
Widespread Custom Permission Use
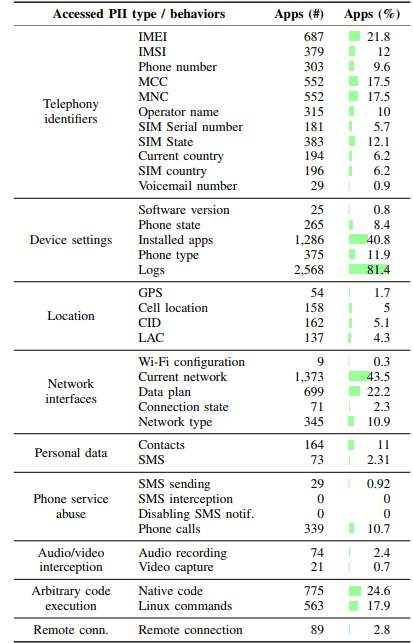
The researchers found 4,845 custom permissions across 108 Android vendors, with three vendors accounting for 68% of permissions. As expected, those vendors are Samsung, which accounts for 41%, Huawei, at 20%, and Sony at 7%. These types of permissions let actors bypass Android’s permission model to gather data without user consent.
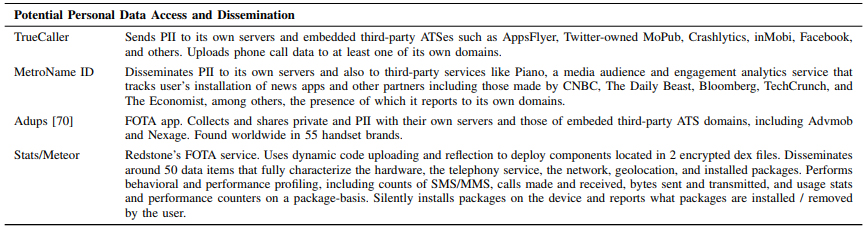
“The study shows, on the one hand, that the permission model on the Android operating system and its apps allow a large number of actors to track and obtain personal user information,” reads the study. “At the same time, it reveals that the end user is not aware of these actors in the Android terminals or of the implications that this practice could have on their privacy. Furthermore, the presence of this privileged software in the system makes it difficult to eliminate it if one is not an expert user.” They found that several VPN solutions that could let vendors monitor user’s traffic, custom Facebook permissions that automatically download Instagram, and more. Further, permissions in some Huawei devices could be used to geolocate users without permission from Android.
The group obtained the information from an app that crowdsourced data from 1,700 android devices. On some of those devices, they found popular Android malware in the system partition aimed at performing bank fraud, subscribing to premium services, and more. “Modern smartphones include system software designed by their manufacturers to ensure their devices run properly and meet user expectations,” said Google to TechCrunch in response to the study. “Researchers’ methodology is unable to differentiate pre-installed system software — such as diallers, app stores and diagnostic tools–from malicious software that has accessed the device at a later time, making it difficult to draw clear conclusions.”